Description
Context:
- Pakistan-linked hackers are targeting critical infrastructure PSUs in India, a report says.
Report findings:
- An advanced persisted threat (APT) group with links to Pakistan is targeting critical Indian infrastructure of public enterprises, according to a report by cybersecurity firm Seqrite.
- Seqrite have alerted government authorities, and are working with them to keep potential targets safe.
- Firms related to telecommunications, finance and power have been targeted.
- The research firm suspects the attack to be a cyber-espionage campaign launched to get access to sensitive information to gain a competitive advantage against India.
- As part of the campaign, attackers are sending out phishing emails with government-themed documents in an attempt to lure targets into opening the attachments.
- The malicious actors have enhanced the attack tools and methods, as compared to last year, to make detection difficult, it noted.
- The final payload can capture sensitive information including screenshots, keystrokes, and files from affected system. It can also execute commands specified as part of instructions from C2 servers.
- The group can potentially steal critical intel from the government agencies and their subsequent bodies.
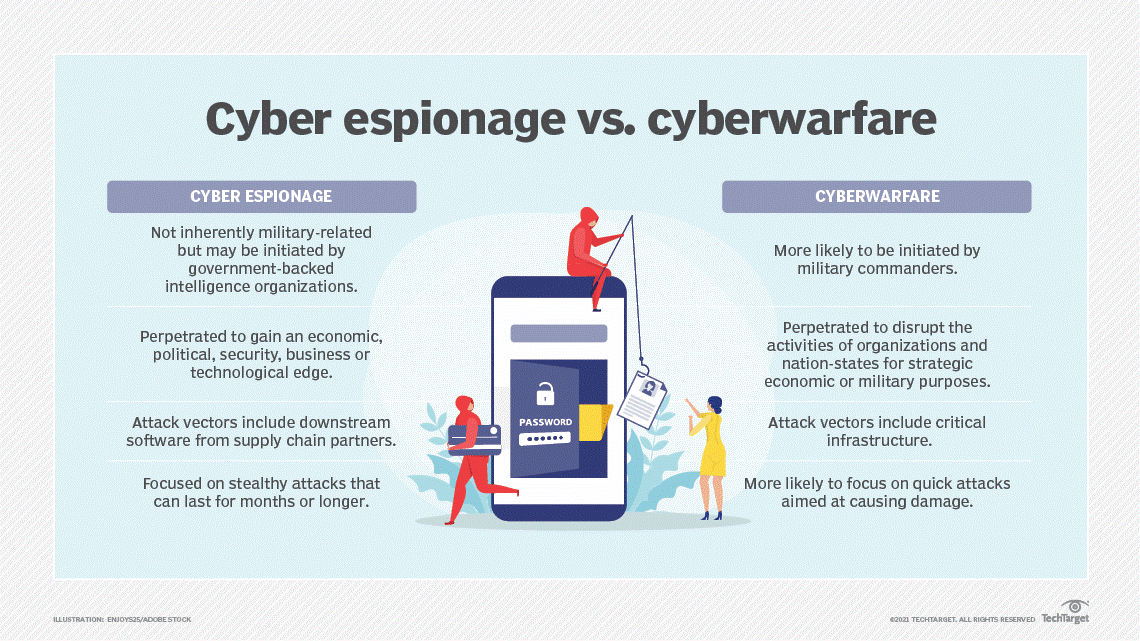
What is Cyber Espionage?
- Cyber espionage, or cyber spying, is a type of cyberattack in which an unauthorized user attempts to access sensitive or classified data or intellectual property (IP) for economic gain, competitive advantage or political reasons.
Why Is Cyber Espionage Used?
- Cyber espionage is primarily used as a means to gather sensitive or classified data, trade secrets or other forms of IP that can be used by the aggressor to create a competitive advantage or sold for financial gain.
- In some cases, the breach is simply intended to cause reputational harm to the victim by exposing private information or questionable business practices.
- They may also be deployed in conjunction with military operations or as an act of cyber terrorism or cyber warfare.
- The impact of cyber espionage, when it is part of a broader military or political campaign, can lead to disruption of public services and infrastructure, as well as loss of life.
Cyber Espionage Targets
- The most common targets of cyber espionage include large corporations, government agencies, academic institutions, think tanks or other organizations that possess valuable IP and technical data that can create a competitive advantage for another organization or government.
- Targeted campaigns can also be waged against individuals, such as prominent political leaders and government officials, business executives and even celebrities.
Cyber spies most commonly attempt to access the following assets:
- Research & Development data and activity
- Academic research data
- IP, such as product formulas or blueprints
- Salaries, bonus structures and other sensitive information regarding organizational finances and expenditures
- Client or customer lists and payment structures
- Business goals, strategic plans and marketing tactics
- Political strategies, affiliations and communications
- Military intelligence
Common Cyber Espionage Tactics
- Most cyber espionage activity is categorized as an advanced persistent threat (APT).
- An APT is a sophisticated, sustained cyberattack in which an intruder establishes an undetected presence in a network in order to steal sensitive data over a prolonged period of time.
- An APT attack is carefully planned and designed to infiltrate a specific organization and evade existing security measures for long periods of time.