Description
Disclaimer: Copyright infringement not intended.
Context
- Apple, announced it will be increasing the number of data points protected by end-to-end encryption on iCloud from 14 to 23 categories.
.jpg)
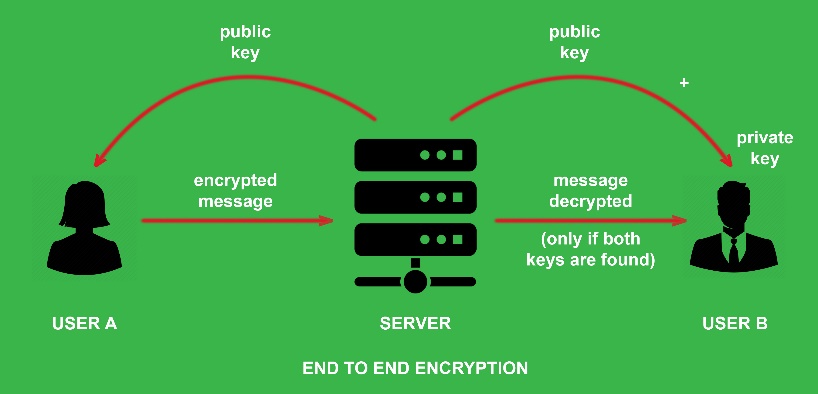
What is end-to-end encryption?
- End-to-end encryption is a communication process that encrypts data being shared between two devices.
- It prevents third parties like cloud service providers, internet service providers (ISPs) and cybercriminals from accessing data while it is being transferred.
- The process of end-to-end encryption uses an algorithm that transforms standard text into an unreadable format. This format can only be unscrambled and read by those with the decryption keys, which are only stored on endpoints and not with any third parties including companies providing the service.
- End-to-end encryption has long been used when transferring business documents, financial details, legal proceedings, and personal conversations. It can also be used to control users’ authorisation when accessing stored data, which seems to be what Apple intends to do.
Where is it used?
- End-to-end encryption is used to secure communications. Some of the popular instant-messaging apps that use it are Signal, WhatsApp, iMessage, and Google messages. However, instant messaging is not the only place where user data is protected using end-to-end encryption. It is also used to secure passwords, protect stored data and safeguard data on cloud storage.
What does it mean for users?
- End-to-end encryption ensures that user data is protected from unwarranted parties including service providers, cloud storage providers, and companies that handle encrypted data.
- The data can only be accessed with access to the device passcode, password, recovery contact, or recovery key. The technology also makes it harder for service providers to share user information from their services with authorities.
- However, end-to-end encryption does not protect metadata, which includes information like when a file was created, the date when a message is sent and the endpoints between which data was shared.
.jpg)
https://www.thehindu.com/sci-tech/technology/what-is-end-to-end-encryption-and-why-are-tech-companies-focusing-on-it/article66251153.ece#:~:text=End%2Dto%2Dend%20encryption%20is,while%20it%20is%20being%20transferred.






.jpg)





