Description
Disclaimer: Copyright infringement not intended.
Context
The 'SIM swap scam' has emerged as a sophisticated cybercrime technique aimed at gaining unauthorized access to individuals' bank accounts and financial information.
Details
Understanding the Basics
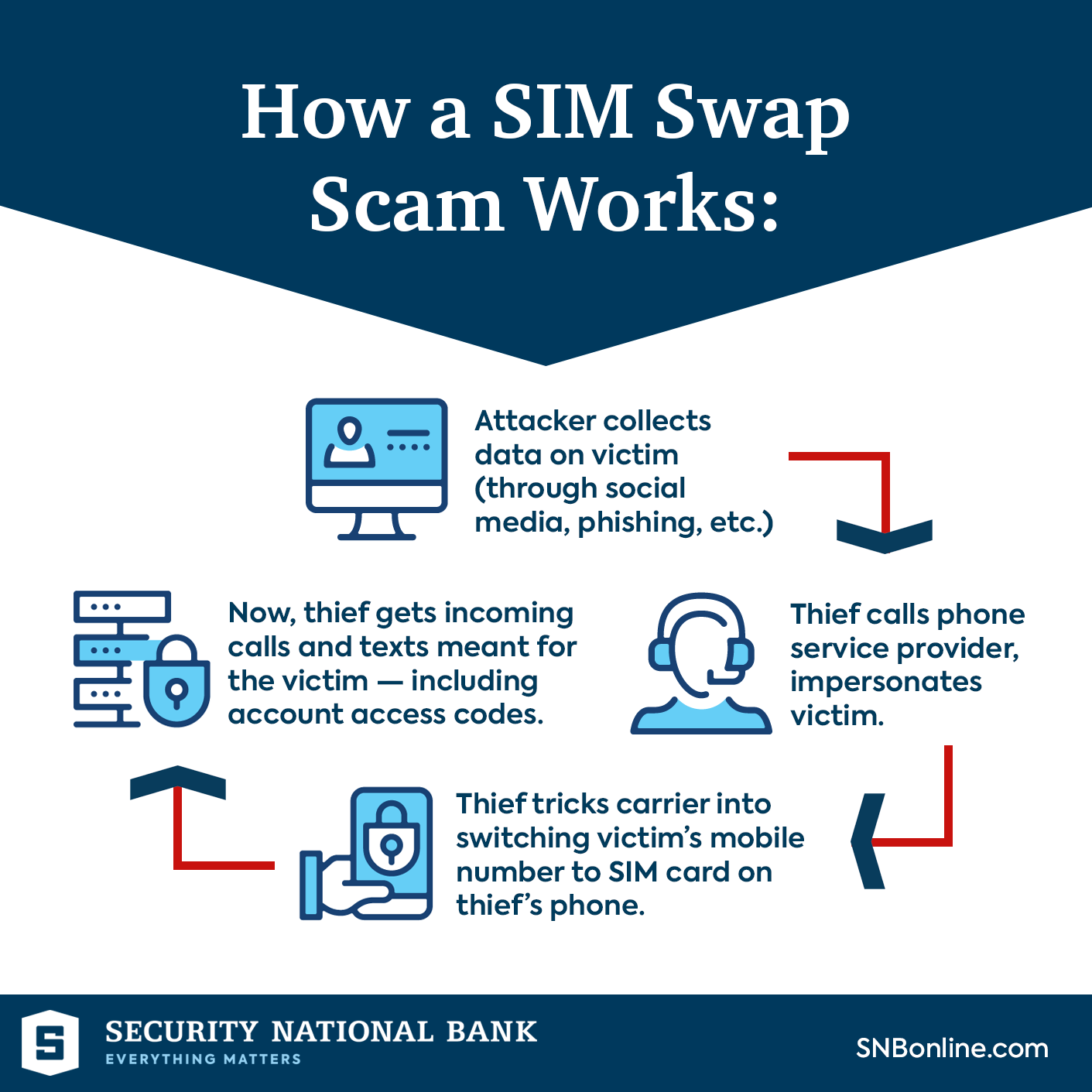
- Definition: A SIM swap scam involves fraudsters deceiving mobile network operators into transferring a victim's phone number to a SIM card under their control.
- Objective: The scam aims to gain access to the victim's personal information, financial accounts, and other sensitive data.
- Technique: Scammers often exploit security vulnerabilities, social engineering, or insider cooperation to execute a SIM swap.

Understanding the SIM Swap Scam
- Phishing and Vishing Attacks: Cybercriminals acquire personal information, including phone numbers and bank details, through phishing emails or vishing calls, exploiting unsuspecting individuals and gaining access to sensitive data.
- Duplication of SIM Card: Scammers visit mobile operator outlets, posing as victims with forged ID proofs, and obtain duplicate SIM cards, enabling them to intercept banking messages and OTPs.
- Unauthorized Access to Bank Accounts: With control over the victim's phone number, fraudsters use the intercepted data to gain unauthorized access to bank accounts and conduct fraudulent transactions.
Warning Signs of a SIM Swap Scam
- Sudden Loss of Network Signal: If your phone suddenly loses signal and displays "Emergency Calls Only," it could indicate a SIM swap in progress.
- Inability to Access Accounts: If you suddenly cannot access your email, social media, or financial accounts despite entering the correct credentials, your SIM might have been swapped.
- Unusual Messages from Service Providers: Notifications or messages from your mobile provider about a SIM card change, despite not initiating any such request, could signify a potential scam.
Techniques Employed by Scammers
- Phishing: Scammers may use phishing emails or messages to trick victims into sharing sensitive information, which they later use to conduct a SIM swap.
- Social Engineering: Fraudsters might impersonate victims to customer service representatives, persuading them to facilitate the SIM swap process.
- Insider Involvement: In some cases, employees within mobile network companies may collude with scammers, enabling them to carry out fraudulent SIM swaps.
Impact and Consequences of SIM Swap Scams
- Financial Loss: Scammers can gain access to the victim's financial accounts, leading to unauthorized transactions and substantial financial losses.
- Identity Theft: With access to personal information, scammers can perpetrate identity theft, jeopardizing the victim's privacy and security.
- Data Breach: The scam can lead to the exposure of sensitive data, including personal and financial information, putting the victim at risk of further exploitation.

Prevention and Protection Measures
- Use Two-Factor Authentication (2FA): Implement 2FA with an authentication app rather than relying solely on SMS-based verification.
- Monitor Account Activity: Regularly monitor your financial and online accounts for any suspicious activities or unauthorized transactions.
- Secure Personal Information: Be cautious about sharing personal information online and avoid responding to unsolicited messages or calls requesting sensitive data.
- Contact Service Providers: Immediately inform your mobile network provider if you suspect a SIM swap scam and follow their instructions for securing your account.
- Stay Informed: Keep yourself updated about the latest cybersecurity threats and scams to stay vigilant and protect your personal information effectively.
|
PRACTICE QUESTION
Q. Discuss the phenomenon of the SIM swap scam, highlighting its intricate mechanisms and the implications of this cyber fraud on individuals and financial institutions. Elaborate on the preventive measures that can be adopted to mitigate the risks associated with the SIM swap scam, emphasizing the role of public awareness and technological vigilance in ensuring cybersecurity. (250 Words)
|
















