





Disclaimer: Copyright infringement is not intended.
Context:
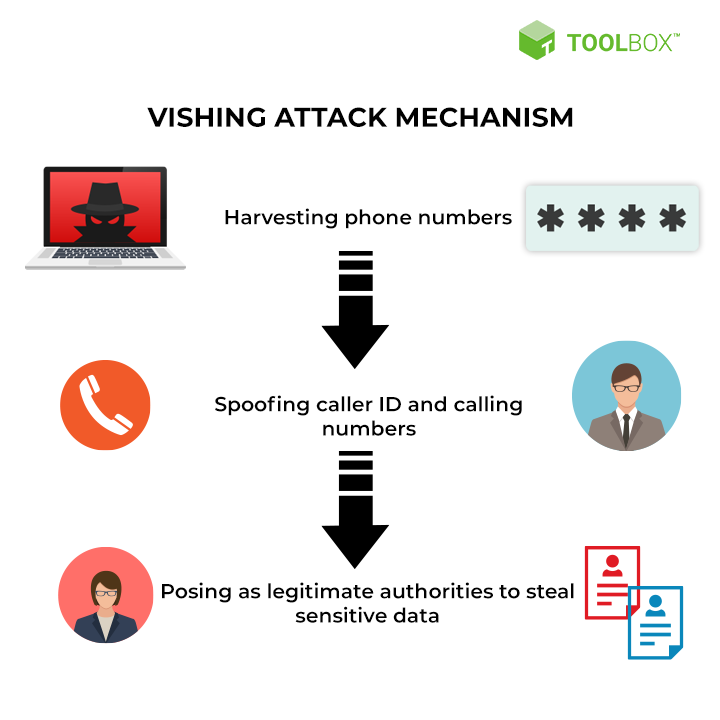
Vishing:
Cyber attacks:
https://www.iasgyan.in/daily-current-affairs/cyber-attacks
Source:
|
PRACTICE QUESTION Q) Consider the following statements about the
Which of the above statements is/are correct? a) 1 only Answer: b) Explanation:
|










© 2025 iasgyan. All right reserved