ZERO DAY EXPLOIT

Disclaimer: Copyright infringement not intended.
Context
- Officials have asked iPhone users to update their devices with 15.6.1 to avoid zero-day exploit vulnerabilities.
About
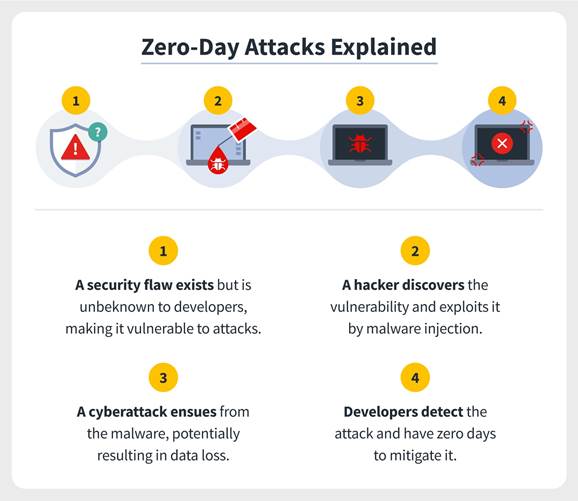
- A zero-day (0day) exploit is a cyber-attack targeting a software vulnerability which is unknown to the software vendor or to antivirus vendors. The attacker spots the software vulnerability before any parties interested in mitigating it, quickly creates an exploit, and uses it for an attack. Such attacks are highly likely to succeed because defenses are not in place. This makes zero-day attacks a severe security threat.
- Example: Pegasus, the spyware developed by the Israeli company NSO Group, also used zero-day vulnerabilities.
- Typical targets for a zero-day exploit include:
- Government departments.
- Large enterprises.
- Individuals with access to valuable business data, such as intellectual property.
- Large numbers of home users who use a vulnerable system, such as a browser or operating system. Hackers can use vulnerabilities to compromise computers and build massive botnets.
- Hardware devices, firmware and Internet of Things (IoT).
- In some cases, governments use zero-day exploits to attack individuals, organizations or countries who threaten their natural security.
- Because zero-day vulnerabilities are valuable for different parties, a market exists in which organizations pay researchers who discover vulnerabilities. In addition to this ‘white market’, there are gray and black markets in which zero-day vulnerabilities are traded, without public disclosure, for up to hundreds of thousands of dollars.




1.png)
